The problem of mobile anonymity
Dystopia is in full swing in Europe, and achieving true anonymity from mobile devices is a big problem. The picture below shows that most countries require mandatory registration of SIM cards on the national ID or passport. This means that all mobile operators in a given state (and, of course, the state institutions themselves) have complete location information of their citizens using local SIM cards. The official reason for the mandatory registration of SIM cards is to fight crime and organized crime. Unfortunately, there is no evidence that compulsory registration of SIM cards leads to lower crime (I recommend the study Mandatory registration of prepaid SIM cards – Addressing challenges through best practice). On the contrary, there is evidence that totalitarian governments repeatedly abuse mandatory registration of SIM cards to monitor their critics and opponents.
That is why I personally consider it important to use all legal means to avoid the widespread spying that compulsory SIM card registration entails.
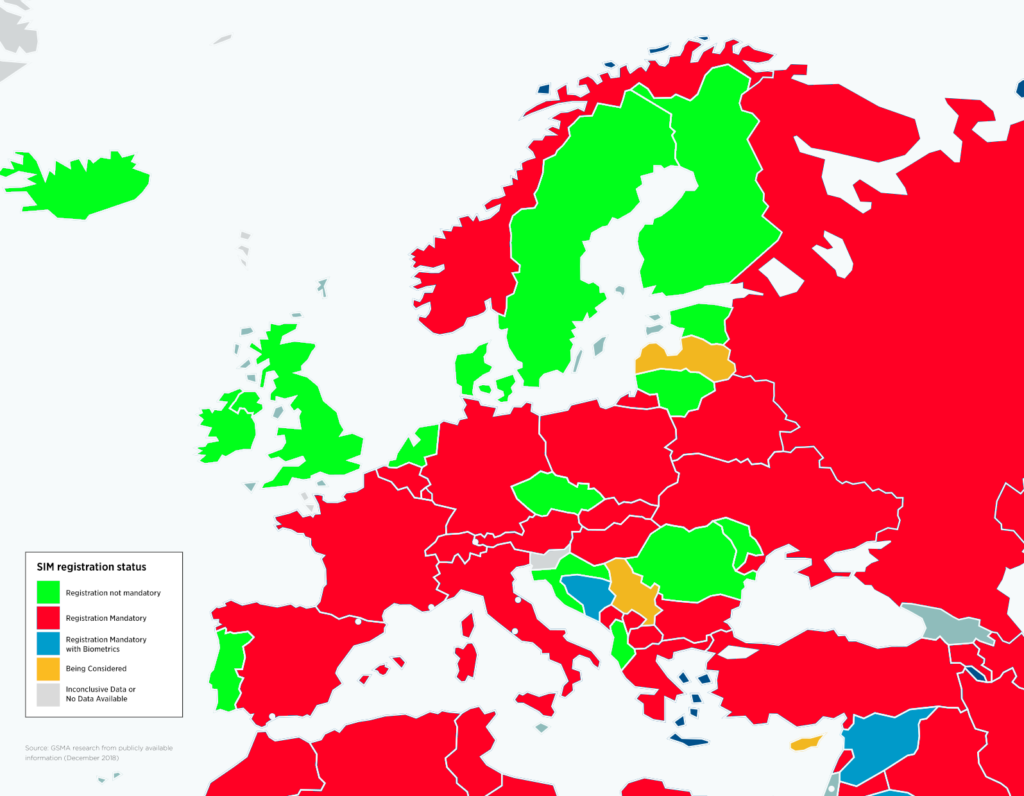
As we can see, there are still countries (such as the Czech Republic, the UK, and others) where it is still possible to buy an anonymous SIM card without the need to register. The problem arises when you insert this SIM card into a non-anonymous phone. One whose identifier (called IMEI) is already known by the mobile operator – which means that you have used this phone with a non-anonymous SIM card in the past or that when you bought this phone, the retailer recorded its IMEI and linked it to your person or company. In this case, you are de-anonymised, and the mobile operator (and indirectly the state) can identify and locate you again.
If you want a higher degree of anonymity, you need not only an anonymous SIM card, but also an anonymous phone
(i.e. a phone that has been purchased anonymously, for example for Bitcoin Lightning or Monero).
De-anonymising an anonymous phone
Unfortunately, having a completely anonymous SIM card and an anonymous phone may still not help you – mainly if you use the combination (anonymous SIM card + anonymous phone) for a long time. Carry and repeatedly use this anonymous phone with an anonymous SIM card in the same places (your home, work, customer, etc.). The mobile operator will see repeating patterns that will again deanonymize you. It will see the IMEI / IMSI of the same anonymous phone that moves daily on the same route between point A – your work and point B – your home. A quick explanation – IMEI is something similar to a phone’s MAC address; IMSI is the unique identifier of each user on a mobile network, one of several pieces of information stored on the SIM card, not to be confused with ICCID, which is the SIM card identifier.
The solution is to have lots of anonymous SIM cards and lots of anonymous phones.
And use a new anonymous SIM card in a new phone every day (or every few hours) in a different place.
Don’t carry the same route over and over on the same SIM card with the same phone.
Achieving a high level of operational security is difficult – you have to buy enough anonymous SIM cards (and even in the Czech Republic, if you want to buy a large number of them, they try to get personal information from you) and enough anonymous phones (which can be very expensive, since such a phone is disposable and you have to throw it away every few days).
Another alternative is to not use a mobile device with IMEI/IMSI and only log in via local wifi networks. This is the most straightforward and most highly secure approach – unless you don’t mind being offline while you move from one place where there is wifi to another place where there is wifi.
Instead of lots of anonymous SIM cards, lots of anonymous eSIMs
Although it is impossible to buy an anonymous SIM card in Slovakia or other countries worldwide, it is still relatively easy to buy an anonymous eSIM card (eSIM technology is supported by most modern phones). Many global eSIM providers allow this in exchange for cryptocurrencies, such as https://silent.link/, which supports Bitcoin Lightning or Monero. There are cheaper alternatives where it is possible to pay with Bitcoin or other altcoins, such as https://www.keepgo.com (probably the cheapest) or https://www.bitrefill.com/us/en/esims/ (which also accepts the relatively anonymous Bitcoin Lightning).
It is, therefore, possible to purchase any number of anonymous eSIMs anonymously – prices start from €2-3 per eSIM so that you can use a different eSIM every day. When you pay with Bitcoin Lightning, the payment is accepted instantly, and you can activate your new eSIM card immediately on your phone within a minute.
Instead of a bunch of phones, one device that allows change of IMEI
WARNING: Changing the IMEI of your phone / 4G wifi router is illegal in many countries. As long as this is your case, don’t break the law!
Being anonymous and changing your phone to a new one daily is expensive and challenging. Not only is it not enough to pay for the phone, but you also need to be able to buy it anonymously, and with repeated physical deliveries and purchasing a new phone, the likelihood of you being deanonymized increases.
The solution is to get a device that allows you to change the IMEI, the phone’s hardware identifier that makes each phone unique. As mentioned above, many countries prohibit changing the IMEI, so check the situation in the country where you plan to make the change before you take this step.
Two (relatively) well-maintained devices on the market allow IMEI changes:
1. Nokia 8110 4G (also known as Banana phone), which can be bought new on eBay for around 70 EUR.

This phone does not allow you to change the IMEI in the original firmware – you need to temporarily root the phone and then upload the Wallace Toolbox module, which will add a new menu to the phone:
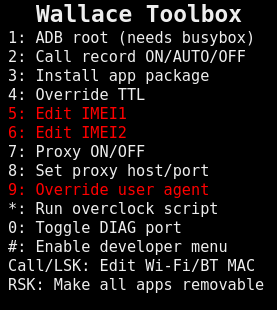
Then, you can easily change IMEI1 and IMEI2 (this is a dual SIM phone, so it is possible to change it for both slots).
Using a completely random IMEI is not a good idea because it can be identified as randomly generated. Therefore, it is better to use a random IMEI from a defined range of phone manufacturers themselves – the following application imeichanger.py by Amir Taaki, can be used for this.
To make the whole anonymization make sense, after changing the IMEI, you need to turn off the phone, insert a new anonymous SIM card, change your physical location, and boot the phone with the new IMEI and the new anonymous SIM card (at this point the phone will appear to the GSM network as a brand new phone with a new SIM card). It is recommended to change the location so that the operator does not see that a new IMEI/IMSI has suddenly appeared where the old IMEI/IMSI disappeared and thus cannot link it.
I should point out that the Nokia 8110 4G allows you to do a regular wifi hotspot, so if you use, for example, Czech or UK SIM cards, you can enjoy decently anonymous Internet (of course, don’t forget about other anonymizing tools like Tor, VPN, etc. at a higher layer).
2. Nitro Wall NW750, which you can buy for 249 EUR.
Nitro Wall NW750 is a branded Mudi 4G LTE portable router (GL-E750) enhanced with IMEI change functionality. If you want to save money, buy the Mudi 4G LTE portable router (GL-E750) for 106 USD and install the IMEI change module yourself. This module is called blue-merle, and you can download it here.
The blue-merle module allows either completely random IMEI randomization or deterministic IMEI randomization, where the IMEI generated by the pseudo-random generator is always the same for a given SIM card IMSI (so the same anonymous SIM card always has the same IMEI).
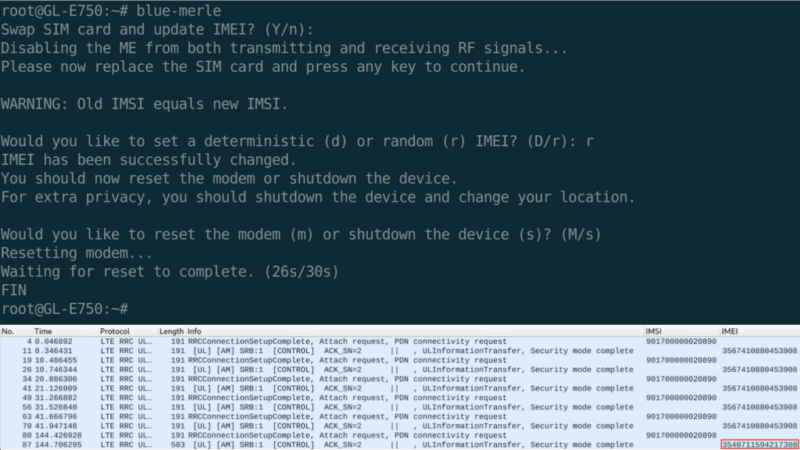
The blue-merle module to change the IMEI is activated by default via the local link https://192.168.8.1/cgi-bin/luci/admin/network/blue-merle after logging into the interface as root.
But devices that can change IMEI do not support eSIM!
All available devices on the market that allow changing the IMEI only support physical SIM cards. Not eSIM. Buying and installing new anonymous physical SIM cards is laborious and expensive (and runs the risk of deanonymisation if the process is repeated).
But there is a solution: https://esim.me/, a physical SIM card that allows you to emulate any eSIM. The cost of this device is between 25 and 70 EUR, depending on how many eSIM profiles you want to manage within a single SIM card. First, you need to insert the ESIM.ME physical SIM card into a regular Android with the appropriate ESIM.ME application, which will “program” the SIM card for you. This means you download the QR code of your new eSIM you just purchased and activate it. Beware, this Android phone must also be anonymous with a random IMEI and always in a different location so you don’t de-anonymize yourself. Similarly, I recommend downloading the ESIM.ME app through an anonymous Google account through the Aurora Store. Using ESIM.ME requires registration, i.e., entering your personal information and an email, which is validated. To remain anonymous, use random personal information and an anonymous email.

You insert the thus-activated physical ESIM.ME card with your favorite anonymous eSIM card (Silent.Link, KeepGo, BitRefill) into your anonymous device that allows you to change the IMEI (Nokia 8110 4G, Nitro Wall NW750, Mudi 4G LTE GL-E750), where you set the new IMEI. The Nitro Wall NW750/Mudi 4G LTE GL-E750 is preferable to the Nokia 8110 4G for frequent IMEI changes, as it is specially equipped with the hardware to do so.

To change the IMEI securely without the possibility of deanonymisation, the following multi-step process must be strictly followed:
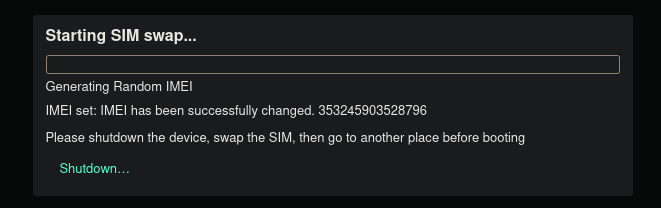
- There is a unique hardware switch on the side of the device (see picture above), which, when toggled, initiates the first phase of the IMEI change. Instructions on the display prompt you to swap the SIM card. You insert a new anonymous SIM card into the device.
- You then put this switch in its original state. At that point, the IMEI on the device will change and physically shut down. At this point, you should change location (so that the operator cannot link your old disappeared IMEI/IMSI to the new IMEI/IMSI that appears at that location).
- Start the phone again – it will boot with the new IMEI and anonymous SIM card.
When you want to change the IMEI/SIM again, repeat the procedure from step 1.
Further safety recommendations
Ensuring maximum anonymity when accessing the Internet on mobile devices is not easy, and the following security guidelines should be followed:
- All necessary physical devices (Nokia 8110 4G, Nitro Wall NW750, Mudi 4G LTE GL-E750, ESIM.ME, etc.) must be delivered to an anonymous address that is not connected to you.
- All payments for the necessary physical devices and SIM / eSIM cards must be anonymous – either for cash or cryptocurrency (which is not connected to you; in the case of Bitcoin, I recommend the mixing service Wasabi Wallet ). You can, for example, buy eBay gift cards with Bitcoin Lightning or Monero. Or you can purchase goods on Amazon.com and pay with crypto services like Fold or Moon.
- eSIM services like KeepGo or Bitrefill or activating eSIM.ME requires you to enter personal information and an activation email. The personal data must be randomized (not verified), and the activation email must be anonymous from a secure service (such as ProtonMail).
- Access to all services in this process (ordering devices, ordering eSIMs and activating them, filling out registration forms, reading activation emails, etc.) must be exclusively via Tor or a secure, anonymous VPN.
- When changing the IMEI, it is recommended to switch off the device and change the location so that the operator does not see that where the old IMEI / IMSI has disappeared, a new IMEI / IMSI has suddenly appeared, which could lead to deanonymisation.
- Randomizing MAC addresses (which the blue-merle module does automatically) is also essential.
- Care should also be taken about anonymization and security at higher layers (use Tor, secure VPN, end-to-end encrypted connections).
