Watch a video and read our comprehensive answers:
Describe what Threat Hunting means and why it can be helpful for companies?
On average, adversaries are present within an organization for more than 140 days before they are detected, and it often takes weeks and even months to entirely remove them. The time during which an adversary maintains a continuous presence within an organization is better known as dwell time.
The main goal for hunting is to reduce dwell time. Threat hunting is the proactive and iterative search through endpoints, networks, or datasets to detect suspicious or malicious activities that have evaded detection by existing automated solutions or tools.
Threat hunters focus their efforts on adversaries who are already within the networks and systems of the victim, where hunters have the authority to collect data and deploy countermeasures. Threat hunters hunt the environment for unknown bads, which are those threats that are not typically detected by real-time detection systems.
Hunters are responsible for looking for and identifying known and unknown adversaries within the organization’s assets, then analyzing their actions and behavior to determine their intent and impact.
Threats are human. Threat hunters are interested in the adversaries, not just their tools (such as malware). These adversaries are persistent, have their own techniques, tactics, and procedures, and often evade network defenses. Threats are often identified as advanced persistent threats (APTs), not just because of the adversaries’ capabilities but also because of their ability to initiate and maintain long-term operations against targets.
What kind of information do we need to collect from the customer to do Threat Hunting? Is it a strictly passive phase?
To hunting successfully, the customer must have logs collected (network and host logs). The more information, the better chances to spot threats. Just by looking at the logs, the threat hunter could obtain the information required to discover a threat – depending on the type and quality of the logs. However, an essential part of the threat hunting activity is to enrich the automated analytics (create alerts, rules to trigger incidents) to avoid these threats to evade the current security solutions.
Compared to the traditional incident response and SIEM monitoring many customers already use and have implemented, what is the added value of Threat Hunting for the customer?
The SIEM monitoring and Incident Response teams usually respond to incidents. When the security alerts catch a threat, an incident is triggered; this is a reactive process.
Threat hunting is a proactive process; threat hunters don’t wait until an alert is triggered. They actively search for threats to prevent or minimize damage. The act of threat hunting should essentially test an organization’s capability to detect and respond to threats reliably.
Can you reveal the identity of real attackers?
Most organized threat actors follow certain patterns. They have their own Tools, Techniques, Tactics, and Procedures. Adversaries are likely to move on from their attack artifacts once they become known, so they have an inherently limited lifespan. But it is tough for them to shift to different Techniques, Tactics, and Procedures.
Knowing this, a threat hunter focuses on hypothesis-driven efforts to uncover adversary activity; they focus on data analysis to detect patterns or trends that correspond with the actor’s known behavior.
In the following chart we can see the most well-known Advanced Persistent Threat (APT) Groups and to which Industries they focus their efforts:
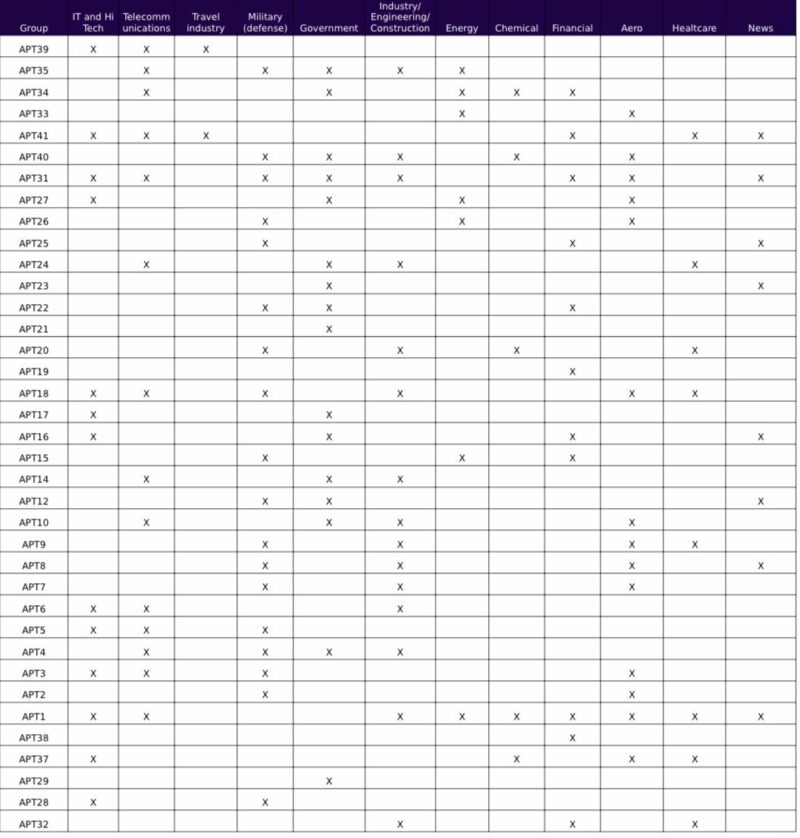
Knowing this information, our threat hunters can specifically focus on revealing which threat actor is behind the attacks. Our clients using our Threat Intelligence service could prepare themselves proactively to avoid any future attacks.
If Threat hunting reveals that the customer is under the long-term attack of the high skilled attacker, should the customer contact the police, or can he try to solve this issue by himself only?
The customer would need to inform the authorities because if their business is attacked, other companies in the same industry could probably be at risk.
The authorities would take action, for example, communicate with other companies to alert them about these attacks. However, this doesn’t mean that the company should leave all the work to the government. Each company will benefit significantly by running internal threat hunting activities to protect their assets, uncover potential attackers and report the investigation results.
What is precisely the “Indicator of Compromise”? How can this information help us?
An “Indicator of Compromise” (IOC) is a piece of forensic data or artifact (IP, domain, C&C server, email address, Registry key, etc.) that belongs to a particular threat. By identifying an Indicator of Compromise, the threat hunter can determine if it belongs to a known threat or threat actor. The client can take proactive actions to block the artifact to prevent further attacks or prevent the compromise of the organization’s assets.
The Indicators of Compromise shouldn’t be confused by “Indicators of Attack” (IOA). An Indicator of Attack focuses on detecting the attacker’s intent, regardless of the malicious artifacts used in the attack.
How is Threat hunting helping us to create multiple hypotheses of a potential incident? Can you tell us some specific examples?
The point of a hunt is not to obtain a true positive malicious event every time, but instead, it is to validate a hypothesis, to answer a question with a definitive yes or no.
All threat hunting processes start with generating hypotheses and then verifying the hypothesis by hunting for the related indicators in all relevant data sources by analyzing logs and marking the hypothesis as true or false.
One of the main methods of generating a hypothesis is the intelligence-driven method. Thus, having good threat intelligence information is likely to increase the number and effectiveness of the hypotheses generated and tested. Here is where Threat Intelligence comes into play.
Example of Hypothesis: My company is in the Gaming industry. This industry is currently being targeted by attackers that operate with C&C servers hosted in North Korea. We want to discover these attackers; we know that they are operating on a Command and Control channel that uses custom encryption on a common network port.
Steps to hunt for this hypothesis:
1. The threat hunter will identify legitimate protocol connections on the various common ports by looking at protocol metadata.
2. The hunter will search for any HTTP protocol while looking at port 80 and the records that exist for a certain period of time and review perimeter connectivity for traffic to North Korean servers.
3. From the output of step 1, the common protocol connections from the session data on the common port will be removed. This should leave uncommon protocol connections on the common port.
4. The threat hunter will look for any valuable data, for example, destination IP, connection duration, bytes transferred, etc.
5. After all the information is investigated, the activity will continue by uncovering new attack patterns and usual Techniques, Tactics, and Procedures to prove or disprove the hypothesis.
The last part of the activity will be to enrich the automated analytics (improve or create new alerts and/or rules to trigger incidents), to improve the detection capabilities of the client.
Why is it necessary to know the “maturity levels” of the customer in the sense of his security posture? How can we use this information?
The Maturity Level of a company can help us determine at which stage in terms of security posture is the client currently positioned. With this information, we can help our clients advance from a minimal security posture to a leading stage. They will rely on automation to improve their data analysis procedures and data collection while growing the security team’s scale and efficiency.
What is the difference between Threat Hunting and Threat Intelligence service?
Threat Intelligence provides the key difference for threat hunters to focus on areas targeted by adversaries. This activity consists mainly of consuming data and producing data and reports as an output.
The Threat Hunting activities rely on data analysis to hunt the environment for unknown bads, which are those threats that are not typically detected by real-time detection systems. Without efficient and proper data provided by the Threat Intelligence service, the threat hunters would find themselves overwhelmed by the massive amount of data they must analyze.
Threat intelligence is analyzed information about the hostile intent, capability, and opportunity of an adversary. With this information, your company not only will prevent future threats but also will improve its cybersecurity strategy and conduct future investment decisions in the right direction.
Threat Hunting seems to be a helpful service. Why should I order it from Nethemba?
In today’s world, every 39 seconds, there is a new attack somewhere on the web. 64% of companies worldwide have experienced at least one form of a cyber attack. Globally, 30,000 websites are hacked daily. Millions of new pieces of malware are created daily. In addition, 60% of all malicious domains on the internet are associated with spam campaigns.
The global median time between a compromise and detection of sophisticated attacks is 99 days. Therefore, every organization should have a threat hunting program, thus adding a significant value to their security programs to help keep the organization in a proactive instead of reactive stance against threats and decrease the detection time.

